Sensitive Data Redaction
Some users of the Sundeck Private Broker may have strict security requirements which require limited sharing of sensitive
Snowflake metadata with the Sundeck Control Plane. When this data is not shared with the Control Plane, these sensitive
fields will appear as redacted in the Reports. When properly configured, the Private Broker is still able to see all
fields which ensure that features like AutoRouting can function as intended.
To enable sensitive data redaction without impacting the functionality of the Sundeck Private Broker, we must ensure that the Private Broker is provided with its own Snowflake credentials and Role that differs from the Control Plane’s Service Account.
The Private Broker requires Snowflake credentials in order to fetch auto-routing metadata from the Native App. Normally, the Private Broker receives short-lived Snowflake credentials from the Sundeck Control Plane, but credentials can also be configured directly. When the Control Plane is configured to redact sensitive data, the Private Broker must be explicitly configured with Snowflake credentials.
A role other than SUNDECK_SERVICE_ACCOUNT must be configured and provided to the Private Broker. If the Private Broker is configured with the data redaction role, auto-routing will be ineffective.
Create a Role, grant that Role to a Snowflake user, and grant the Role the ADMIN Application Role. Substitute the
Snowflake username who should be granted this role for <PRIVATE_BROKER_USERNAME> and the name of the Warehouse for
<WAREHOUSE_NAME> that this Snowflake user should use in the below SQL.
BEGIN
CREATE ROLE IF NOT EXISTS SUNDECK_PRIVATE_BROKER;
GRANT ROLE SUNDECK_PRIVATE_BROKER TO USER <PRIVATE_BROKER_USERNAME>;
GRANT APPLICATION ROLE SUNDECK.ADMIN TO ROLE SUNDECK_PRIVATE_BROKER;
GRANT USAGE ON WAREHOUSE <WAREHOUSE_NAME> TO ROLE SUNDECK_PRIVATE_BROKER;
END;
The following environment variables should be provided to the Private Broker.
SUNDECK_SF_USERNAMEThe Snowflake username.SUNDECK_SF_WAREHOUSEThe Snowflake warehouse which theSUNDECK_PRIVATE_BROKERrole hasUSAGEon.SUNDECK_SF_ROLEThe Snowflake role,SUNDECK_PRIVATE_BROKER.- One form of Snowflake credentials for this user:
SUNDECK_SF_PASSWORDThe Snowflake user’s password.
SUNDECK_SF_PRIVATE_KEYandSUNDECK_SF_PRIVATEKEY_PASSPHRASEThe Snowflake user’s private key (and optional private key passphrase).
For more information on these configuration options, see the Private Broker Configuration documentation.
Validate that the Private Broker auto-routing is successful after changing the configuration before enabling redaction.
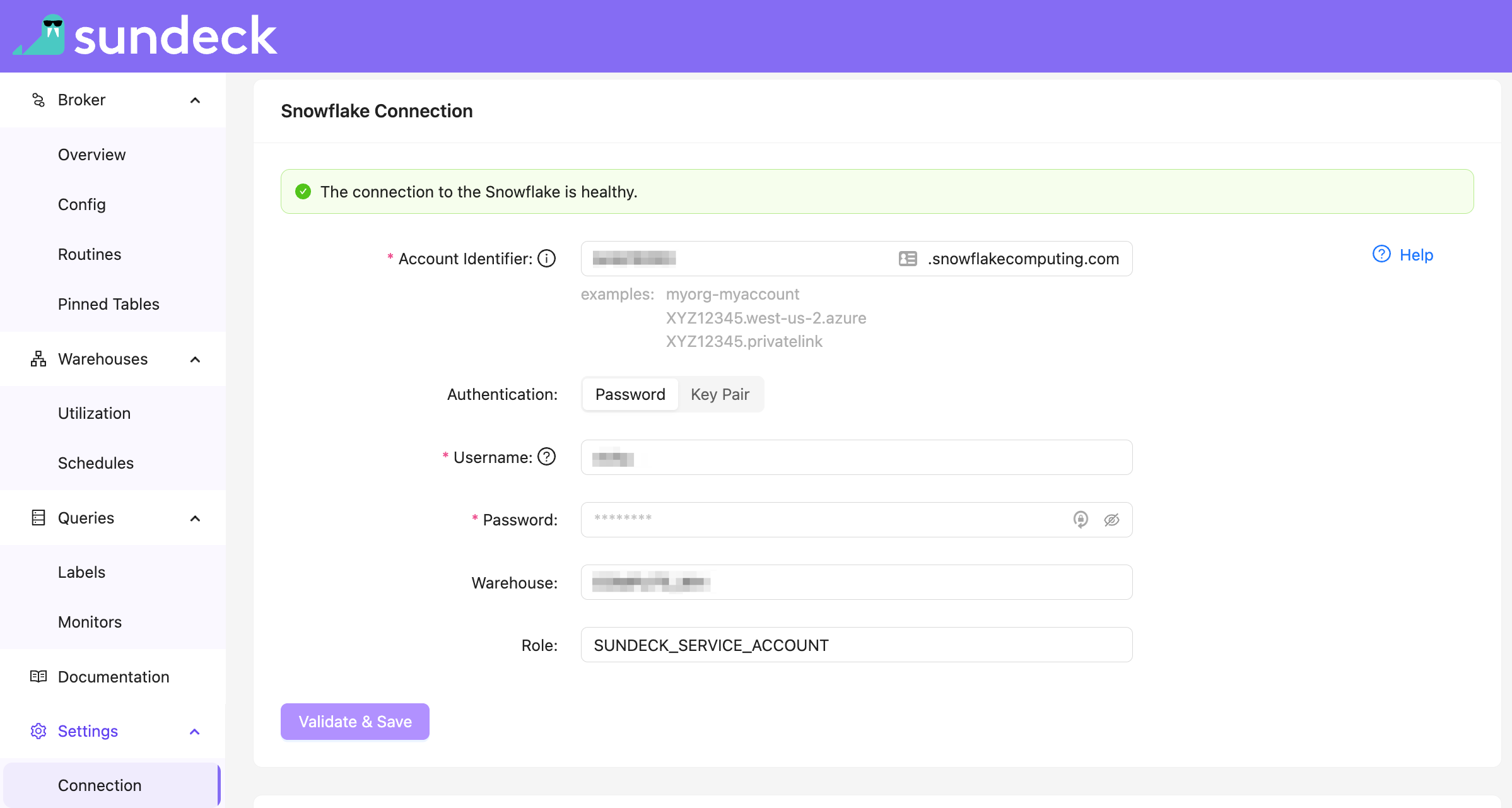
Sensitive data redaction is configured using Snowflake Roles.
- Ensure that the given Snowflake Role for the Sundeck Service Account is configured with the SUNDECK_SERVICE_ROLE Snowflake Application Role.
BEGIN
CREATE ROLE IF NOT EXISTS SUNDECK_SERVICE_ACCOUNT;
GRANT APPLICATION ROLE SUNDECK.SUNDECK_SERVICE_ROLE TO ROLE SUNDECK_SERVICE_ACCOUNT;
END;
- Enable sensitive data redaction in the Sundeck Native Application
CALL SUNDECK.ADMIN.REDACT_QUERY_TEXT_FROM_SERVICE_ROLE();
- Re-configure the Sundeck Service Account (as-needed)
Ensure that the configured Sundeck Service Account uses the role from step 1.
- Re-verify Private Broker Auto-Routing
Restart the Private Broker and verify that queries submitted to the Private Broker are still being Auto-Routed after enabling redaction.
After enabling redaction, consider setting the SundeckBROKER_MODEparameter toPRIVATEto disable queries through the SaaS Broker as they will fail to be auto-routed.
To disable sensitive data redaction, run the following command:
CALL SUNDECK.ADMIN.RESTORE_QUERY_TEXT_TO_SERVICE_ROLE();
The following fields are considered sensitive and can be redacted in Control Plane Reports.
QUERY_TEXT– The full text of a query executed on Snowflake.CLIENT_IP– The IP address where a Snowflake session originated.
